继续说上一篇文章接下来的故事,客户因为个别服务器被大流量 DDoS 攻击导致网络瘫痪,需要对路由器配置 RTBH 功能来实现自动空路由,以避免未被攻击的服务器无法与外界通信。
要想实现 RTBH 功能,需要对 BGP session 配置 import policy 来触发黑洞动作。在配置之前,我们需要做一些准备工作。
拓扑整图如下:
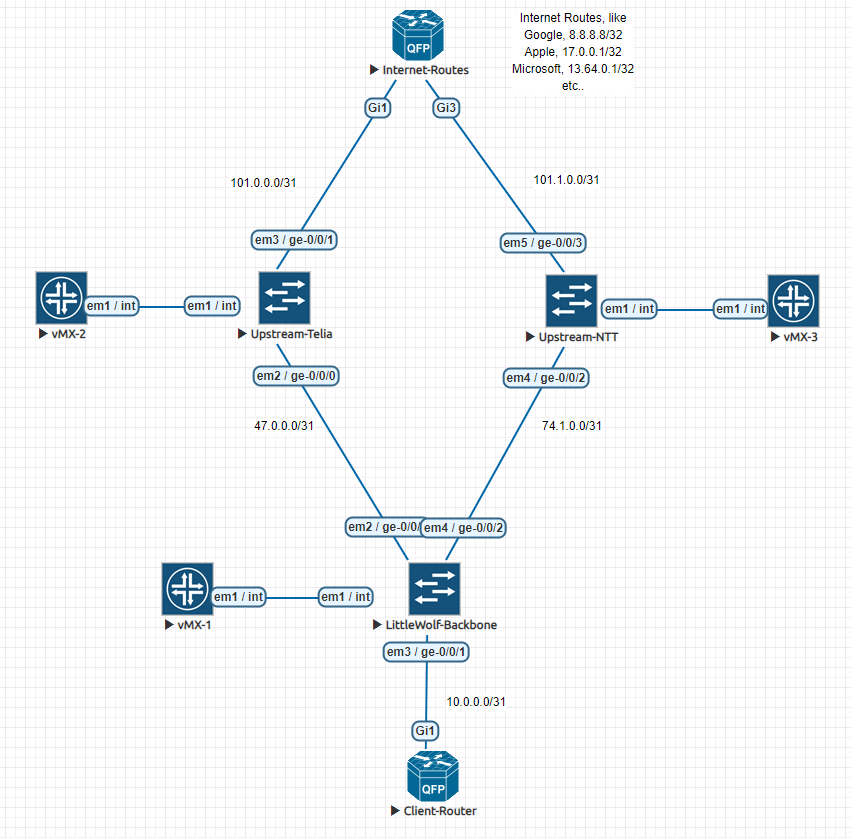
我们要事先准备的事项有:
- 一张已经配置好的网络
- 寻求 ISP 的帮助,从 ISP 获得黑洞路由 community
首先,我们需要先验证路由器的路由表:
Internet-Routes# show ip route bgp
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
Gateway of last resort is not set
45.0.0.0/24 is subnetted, 10 subnets
B 45.1.1.0 [20/0] via 101.0.0.1, 00:23:07
B 45.1.2.0 [20/0] via 101.0.0.1, 00:23:07
B 45.1.3.0 [20/0] via 101.0.0.1, 00:23:07
B 45.1.4.0 [20/0] via 101.0.0.1, 00:23:07
B 45.1.5.0 [20/0] via 101.0.0.1, 00:23:07
B 45.1.6.0 [20/0] via 101.1.0.1, 00:23:07
B 45.1.7.0 [20/0] via 101.1.0.1, 00:23:07
B 45.1.8.0 [20/0] via 101.1.0.1, 00:23:07
B 45.1.9.0 [20/0] via 101.0.0.1, 00:23:07
B 45.1.10.0 [20/0] via 101.1.0.1, 00:23:07
没有问题,客户路由接收正常。
然后,我们需要获得 ISP的黑洞路由 community:
- NTT – 2914:666
- TELIA – 1299:999
现在我们来模拟客户的服务器被攻击的情况:45.125.10.2 受到大流量攻击,我们需要将其流量发送至黑洞来避免网络被完全堵死。配置如下:
root@Littlewolf-Backbone# show | compare
[edit policy-options]
+ community ntt-rtbh members 2914:666; // 定义 NTT 的 community value
+ community rtbh members 65535:666; // 定义内网的 community value
+ community telia-rtbh members 1299:999; // 定义 Telia 的 community value
[edit policy-options]
+ policy-statement customer-rtbh {
+ term rtbh { // 定义黑洞路由规则,若客户发过来的 community 含有黑洞路由则接受。
+ from community rtbh;
+ then accept;
+ }
+ }
+ policy-statement ntt-blackhole {
+ term rtbh { // 定义黑洞路由规则,若检测到发给上游的网段含有内网的黑洞路由 community 则添加 ntt 的黑洞 community
+ from community rtbh;
+ then {
+ community add ntt-rtbh;
+ accept;
+ }
+ }
+ }
+ policy-statement telia-blackhole {
+ term rtbh { // 定义黑洞路由规则,若检测到发给上游的网段含有内网的黑洞路由 community 则添加 telia 的黑洞 community
+ from community rtbh;
+ then {
+ community add telia-rtbh;
+ accept;
+ }
+ }
+ }
[edit protocols bgp group upstream neighbor 47.0.0.1]
- export [ telia-prepend telia-filter bgp-announce ];
+ export [ telia-prepend telia-filter telia-blackhole bgp-announce ]; // 在上游侧应用黑洞路由规则
[edit protocols bgp group upstream neighbor 74.1.0.1]
- export [ ntt-prepend ntt-filter bgp-announce ];
+ export [ ntt-prepend ntt-filter ntt-blackhole bgp-announce ];
[edit protocols bgp group downstream neighbor 10.0.0.0]
- import customer-import;
+ import [ customer-rtbh customer-import ]; // 在下游侧应用黑洞路由接收规则
配置完成,我们告知客户可以发送含有 65535:666 的路由来实现自动阻拦流量,客户发送了携带该 community 的 45.125.10.2/32 路由来将目的地址为该 IP的数据包送进黑洞。
验证骨干路由器路由表:
root@Littlewolf-Backbone> show route receive-protocol bgp 10.0.0.0
inet.0: 22 destinations, 25 routes (21 active, 0 holddown, 1 hidden)
Prefix Nexthop MED Lclpref AS path
* 45.1.1.0/24 10.0.0.0 0 65535 I
* 45.1.2.0/24 10.0.0.0 0 65535 I
* 45.1.3.0/24 10.0.0.0 0 65535 I
* 45.1.4.0/24 10.0.0.0 0 65535 I
* 45.1.5.0/24 10.0.0.0 0 65535 I
* 45.1.6.0/24 10.0.0.0 0 65535 I
* 45.1.7.0/24 10.0.0.0 0 65535 I
* 45.1.8.0/24 10.0.0.0 0 65535 I
* 45.1.9.0/24 10.0.0.0 0 65535 I
* 45.1.10.0/24 10.0.0.0 0 65535 I
* 45.1.10.2/32 10.0.0.0 0 65535 I
inet6.0: 1 destinations, 1 routes (1 active, 0 holddown, 0 hidden)
root@Littlewolf-Backbone> show route advertising-protocol bgp 47.0.0.1 45.1.10.2/32 extensive // 查看发送给 telia 的路由,验证是否已经携带 community
inet.0: 22 destinations, 25 routes (21 active, 0 holddown, 1 hidden)
* 45.1.10.2/32 (1 entry, 1 announced)
BGP group upstream type External
Nexthop: Self
AS path: [138667] 65535 I
Communities: 1299:999 65535:666
可见已经收到客户发来的路由我们骨干网路由器已经发送给了上游,现在检测路由是否已经被阻断。
验证 Internet-router 到 customer-router 的连通性:
Internet-Routes#traceroute 45.1.10.1 source lo0 // 跟踪网关地址 Type escape sequence to abort. Tracing the route to 45.1.10.1 VRF info: (vrf in name/id, vrf out name/id) 1 101.1.0.1 139 msec 123 msec 168 msec 2 74.1.0.0 252 msec 1000 msec 26 msec 3 10.0.0.0 28 msec 22 msec * Internet-Routes#traceroute 45.1.10.2 source lo0 // 跟踪被攻击的服务器地址 Type escape sequence to abort. Tracing the route to 45.1.10.2 VRF info: (vrf in name/id, vrf out name/id) 1 * * * 2 * * * 3 * * * 4 * Internet-Routes#
可见被攻击的服务器成功进了黑洞,流量在 ISP 的路由器上的时候就被 ISP 路由器丢弃了,成功的保证了我们本地网络不会因为攻击流量堵塞链路而导致瘫痪。
这样,配合着之前的 community 配置,一个基本的含有 community 的 IDC 网络配置完成了。